
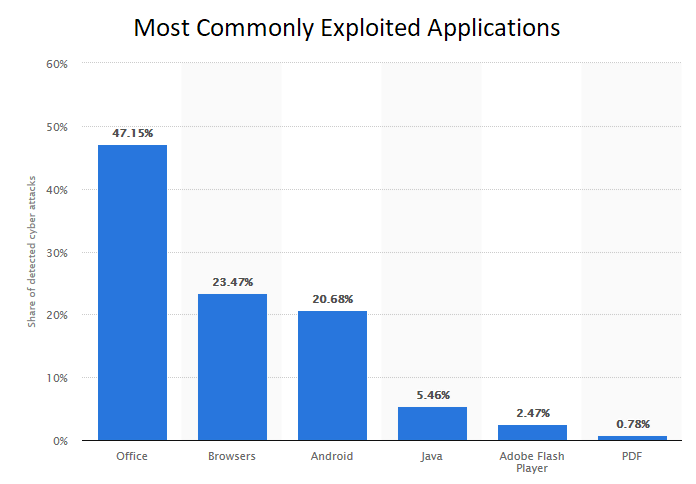
As soon as you have anything of value on your account you should take a moment and look at your approach to key management is sufficient enough. The purpose of this article is to inform and educate by providing real case examples of what can happen and how you can prevent, or at least reduce the risk.
It’s not only your average user that has poor private key management but technical teams as well. There are multiple BPs/Guilds on EOSIO chains, as well as large accounts that have poor key management. This is a careless risk factor... Don't be that guy.
There are a lot of steps that anyone can take to reduce risks involved in managing keys. A bunch of them are really rather simple, and can be performed with little to no means. If this scares you, good, it should. Every year companies are blackmailed for billions of USD, and crypto folks lose millions of funds. A lot of these could be prevented by rather simple measures.. so once again... Don't be that guy, it's not that fun.
Checklist of Basic private key and account management
- Generate your keys on a secure device
- Your everyday computer is likely not secure
- Your phone is likely not secure
- Use a trusted hardware solution (i.ex. yubihsm2, ledger)
- Laminated paper Copy of Private key is usually a good idea
- Don't store owner key in a phone
- Don't store owner key in a device with multiple users
- Don't store owner key in a machine that is online
- Don't store owner key online (or in a remote machine)
- Don't add your owner key to wallets unless you intend to use it and swap it
- Treat the owner key as your biggest secret that no one should know about.
- Don't use random wallets, they can be malicious
- Don't open files from telegram people (even trusted sources)
- Don't use sms or email as your 2fa
- Don’t print your Private key onto a paper, it’s likely logged in the printer.
- Don’t email your private key anywhere
- Don’t expose your Mnemonic seed phrase to any service.
- Only add your active key to trusted devices
- Add custom permission keys for your everyday use, i.ex. claim, vote, games.
- Whenever you had to use the owner key, swap it to a new one
- Double check your downloaded files so they are the correct ones before installing.
- Don't give your private key to ANYONE, EVER.
Common ways to lose your key (and tokens) that are somewhat out of your control
A) Malware logs what you are doing and use it to hack you
B) Malware change the receiver and takes your funds
C) Device is lost or breaks
D) You have weak password
E) The service is storing your password poorly
F) Your passwords/email combination are leaked
G) Trojans can take your clipboard (everything you copy and/or paste)
H) Rootkits installed in your device
I) You enter your mnemonic phrase at a phishing attempt
J) Signing malicious transactions
K) Autofill on field to wrong address
L) Private key is lost and not properly backed up
M) Password is forgotten
N) Using Public WIFI
Generating your Private Keys
- Generating your Keys on a secure device
- Your everyday computer is likely not secure
- Your Phone is likely not secure
Generating your keys on a secure device is as important, if not even more important than how you store them. Because if they are compromised when you generate them... it won't matter how great your storage solution is.
If you have used a website, or a convenient generator on your machine, it is a risk you should not have if you hold tokens that represent a large value for you. Please learn how to generate keys properly or buy a secure hardware wallet.
Your devices you use for social media, gaming, browsing etc are very likely not safe. It doesn't mean you have malware on your device, but it means the risk is increased and that it is possible. Heck, even the WIFI router you connect to can be hacked and it may not matter if you swap device, use VPN or whatever you do to interact with the internet. And if you connect to a public internet... please don't expose your keys or passwords in any way >.<
Just ask yourself this question... if you were a hacker and wanted to reach a lot of people, would you target a single device or a publicly available WIFI connection? Do you trust that your local café has highly skilled IT personnel?
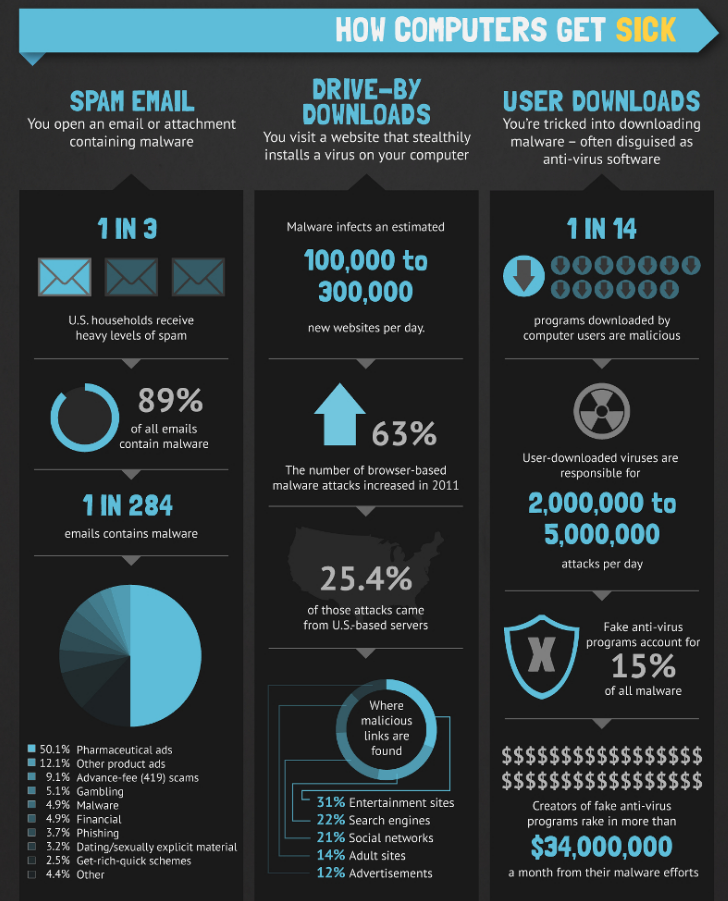
A lot of devices are infected by different malware, not all of them will try to take your password or private key, but we can assume that they are not there to help secure your device.
In this course you will learn how to create a bootable USB that you can connect to any machine and transform it into a safe key generator. Just make sure you also remove wifi, ethernet cables etc. The bootable USB will automaticly have a firewall put up to block all incoming traffic, to help reduce risk.
Still, the keys are only as secure as you treat them.
Storing your Private Keys
- Use a trusted hardware solution (i.ex. yubihsm2, ledger)
For most people, this is a solid solution for storing your keys. As they are very hard to crack. There are still ways to lose your tokens, mainly through signing malicious transactions by connecting to a skimming site or wallet. Although there are some cases of hacked hardware wallets, they usually need to have physical access to the device.
The use of hardware wallets is usually rather simple and by default it reduces a lot of risks. However, you still need to remember and store your password and recovery phrase.. And those two aspects need to be done properly, or it won’t matter if your keys are in a device or on a piece of paper.
- Laminated paper Copy of Private key is usually a good idea
This is actually one of the more safe storing methods of the private keys. It requires whomever wants to steal your tokens to actually locate your note to get them. However, as all options there are risks, which can be mitigated pretty good. Just a simple note will most likely be sufficient, but adding the lamination on top of it will increase the quality of your storage.
If you decide to store your keys on paper, remember that they can easily be copied by a camera without you noticing, it can be damaged by fire, or a spouse that thinks it’s trash. So please create multiple copies of your key and store at different safe locations.
And please, make sure you have the correct key by taking a few extra minutes and adding it once to an fully offline machine, just to make sure you have copied it correctly. Perfect usage of our bootable USB.
- Don't store owner key in a phone
There are TONS of malware directed towards phones. On top of that there are a lot of fake apps listed in the stores on both android and iOS. Android has more of both, but iOS is not without danger. The phone shouldn’t really be treated as a secure and safe device, ever. Only add accounts with limited value, and or keys with special permission to your mobile devices.
This reduces the risk, and you can treat those accounts as hot wallets where you just keep what you intend to use and can lose.
- Don't store owner key in a device with multiple users
Ok, let’s pretend you are flawless and have perfect management of keys and risks. It’s very unlikely that the other person(s) with access to your device is as meticulous as you are. Usually the hacked businesses that get blackmailed for large sums of bitcoin to remove the malware receive the virus from a stupid employee that opens infected mails, click links, download bad software and install that. People don’t manage risk, so expect them to mess up.
- Don't store owner key in a machine that is online
If your machine is online, it can be accessed. There are multiple security holes in a machine these days, and they can be used to access your device. This is more probable the more frequently you use the machine to browse the web, download files and install software. Only use your active key or keys with custom permissions, so that you can reduce the damage if it is compromised. Sucks to lose value, but it sucks more to lose everything.
And please, have different owner and active keys...
- Don't store owner key online (or in a remote machine)
There are multiple cloud services that are used to store private keys… A cloud solution literally means you use someone ELSE'S machine. If you add your owner key to a cloud service, even if one that is more secure, you have to trust that they do not have malicious intentions. Sure, personally I like to trust that people's intentions are good, and that they want to help. But I wouldn’t trust them with my owner key…
I have personally heard of people that store their private keys in google docs, cloud services, dropbox or other storage solutions… I would strongly advise against it. Buy 2 USB thumb drives, move an encrypted file containing your private key to them, and store at two different locations. That will be a way better solution.
- Don't add your owner key to wallets unless you intend to use it and swap it
After reading the above, you know why this is a bad idea… Your Owner key is your admin key. Only enter it if you intend to use it. If you leave it in a wallet, you leave an open attack vector for hackers. Please don’t be that guy.
If you add your owner key to a wallet, and you use your owner key, make sure that you swap it to a new key before you finish what you are doing. You should consider a used owner key as a broken one that needs to be replaced. If you keep multiple owner keys in your account, you can simply remove it.
- Treat the owner key as your biggest secret that no one should know about.
Your owner key is literally your way of proving that the account and tokens on a blockchain is yours. If someone you consider a friend gets hold of it, the account is now theirs. It still falls under theft, but can you prove it? There are multiple stories about people that have stolen private keys of people that were considered friends.
Perhaps you should have some way for your next of kin to find it in case something happens with you.
Interacting with the Blockchain
- Don't use random wallets, they can be malicious
People create wallets for the sole purpose of getting people's private keys and steal their funds. Yes, this is the case.. Browser wallets, desktop wallets, mobile wallets, you name it, hackers want to skim you off your tokens, and they are good at it.
Here are some cases:
- Don't open files from telegram people (even trusted sources)
This is because of multiple reasons, 1, you probably don’t truly know the person you interact with over telegram. If you do know the person, there are multi ways to fake a telegram handle, this is used frequently in scams. And also the account can be stolen and skimmed by copying the users sim card or by malware.
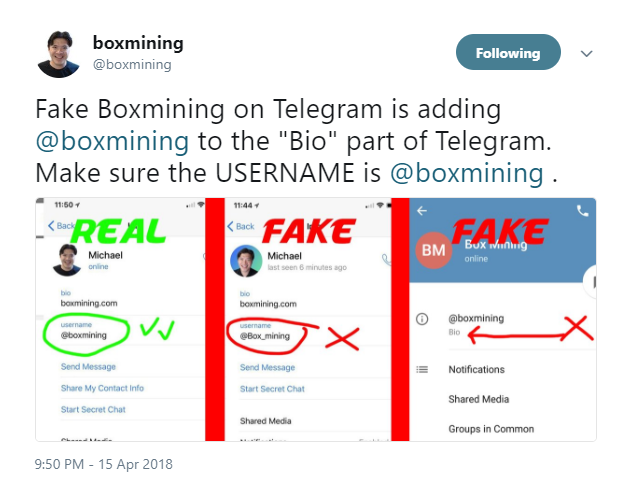
People have been skimmed for hundreds of thousand USD worth of tokens by these tactics, usually the account is really well made, has the same photo (and often the old photos as well), and at a quick glance it is the same account name… by adding it to the bio field and hiding the username field.
One way of noticing this is to use a desktop, open the profile picture and pay attention to the date and time of the uploaded photos, they are often just seconds or minutes apart. AFAIK you can not see the timestamp on a phone.
- Don't use sms or email as your 2fa
SMS and email messages can be intercepted at multiple times. Dan Larimer even lost bitcoins because of an email account recovery on an exchange. And we should understand that the dude that created multiple blockchain solutions understands security. However, this time it was not his fault but the Exchange that had weak security practices. The hackers basicly triggered an email to be sent, read it on the way out and then entered the recovery code to login to the account. They did not even need to login to his email… You can read the full transcript of his talk here: https://sebastiaans.blog/dan-larimer-security-deterministic-code/
If you also just hit google and add “clone sim card”, you will find a lot of different ways to clone one, and this has happened at crypto conferences and gatherings. People have claims that they have lost far more than $1m on these attacks, e.g.: https://stupen.com/business-2019-news/pping-hack-targeo-execs/
Sometimes they don’t even need to hack a device, but just call the support and pretend to be the person.
In short, don’t trust that your phone number is a safe way to verify yourself…
- Don’t print your Private key onto a paper, it’s likely logged in the printer.
Almost all printers on the market now are so called “smart” printers. They use wireless communication, can accept email printouts and work from phones etc. All convenient solutions come with weaknesses, and one of them is that your printer is not a secure device. It logs everything you print, and this means if you print it, someone can fetch it.. So please, do not print it, write it down by hand. Or use one of the old school printers that use a cable and are that are dumb enough not to store your key.
- Don’t email your private key anywhere

Your emails literally go through multiple servers and can be logged and accessed at each of them. If they are not end to end encrypted, you pretty much write your key on a paper and just leave it at a bus stop.. Don’t do that either.
- Don’t expose your Mnemonic seed phrase to any service.
Treat your Mnemonic seed phrase with respect!
Don't enter it anywhere except the same place as you generated it. And only ever do that if you need to RECOVER your shit. People get scammed over and over by entering or poorly storing these phrases..
Please, don't make the mistake of dropping them into a random web service or questionnaire... This happens all the time.
- Only add your active key to trusted devices
Make sure the device you enter your active key into is a device you trust and try to follow best practice... You can never be safe if you use the device, but at least you can reduce the risk by being smart, or at least not being dumb.
If you have a device that only you ever use, this is supposed to be your "trusted device", but only if you don't act reckless.. Don't download everything you see, don't enter to random sites, don't open and click all links in emails, well, don't click, open, download or visit anything you do not intend to do.
If your key is compromised, hopefully your tokens are staked, that way they are locked for 72 hours and you have enough time to reinstall your device, find your owner key, enter it, swap your active key, secure your tokens and in the process of course swap your owner key to a new one.
Staked tokens is a GREAT security aspect that gives you 3 days to react and protect your stuff.
Best practices in General (Don’t regret being stupid)
- Add custom permission keys for your everyday use, i.ex. claim, vote, games.
This is rather simple to do, doesn’t require a lot of knowledge and there are well written guides available, e.g. ours that you can find here: https://waxsweden.org/courses/add-custom-permission-to-your-account/
By using custom keys, with specific use cases in your devices, your risk is minimal as they can only ever perform the EXACT calls that you allow with that key. I.ex. If you create a key that is only allowed to sign transactions to vote, it will not ever be able to do anything else.
To assign specific keys, you need to point to the account with the contract and the action you will allow to be made, I.ex. ‘ eosio::voteproducer ‘ , this will allow you to execute the voteproducer action on eosio, which is what you do to vote on the blockchain.
- Whenever you had to use the owner key, swap it to a new one
This is one of the more powerful features that come along the EOSIO account system. Since your tokens are connected to your account name rather than the key pair (as is the case in bitcoin, ethereum etc), you are actually able to swap your keys as much as you like.. Well, as long as you keep your keys available. Not that the keys are used for your account, but some projects take snapshots of the account status on chain for their projects and forks, and if that is the case, they may actually add accounts with your old key set, this is the case for Telos when they used the genesis accounts from EOS.
Back to the subject, swapping keys, why?
Because they can be compromised, and the owner key is your admin key. This is THE KEY that gives you full control of your account. You can do anything you want with your account using this key, I’m pretty sure you can even summon minions with it.

Swapping the key is great, as the new one is of course generated on a safe device and never entered into a connected machine, as you know this is how to operate ;).
And actually, you should add multiple owner keys, and you are able to remove one, this will make your life easier, plus you will be able to store the keys at different locations.
An example of how that can look is the following testnet account: https://wax-test.bloks.io/account/noobtestings#keys
- Double check your downloaded files so they are the correct ones before installing.
First, Only ever download stuff from secure sources… Secondly, even if you download from a source you trust, they can be compromised and you are best off to verify the checksum. Some products publicly list the checksums to make sure the file you download is the file you are supposed to have downloaded. The checksum is a hash that you can double check on your device after download.
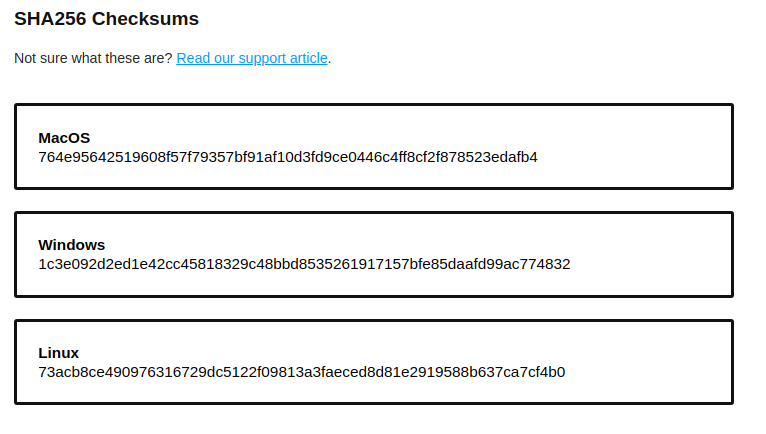
When I check the Windows file on my machine I get the following:
anders@laptop ~/s/M/satter> sha256sum win-scatter-12.0.0.exe 1c3e092d2ed1e42cc45818329c48bbd8535261917157bfe85daafd99ac774832 win-scatter-12.0.0.exe
And as this is the same as the publicly listed sum, I can verify that I got the same. Yes.. the sum you see on the page can be tempered with.. But it’s hard to reduce all risk, completely… At least you are better off than not verifying the file.
- Don't give your private key to ANYONE, EVER.
This is obvious for most… but scammers still get their hands on people's private keys by playing on their trust. DO NOT EVER, IN AN SITUATION give your private key to anyone. Perhaps it’s ok if someone has a gun to your head… but hopefully that’s not your everyday scenario.
Common ways to lose your key (and tokens)
that are somewhat out of your control
A) Malware logs what you are doing and use it to hack you
There can be malwares that log your passwords, activities, search results and much more. These can come in many shapes and forms, including as browser addons. Browser add ons is one case that seems to be growing and easy to overlook. Something boxmining likely had to suffer recently: https://twitter.com/boxmining/status/1237372876908462080
Be careful when you install any software, addons are not an exception.
More to nerd if you find it interesting:
https://www.coindesk.com/browser-extensions-can-help-scammers-steal-your-bitcoin-casa-ceo
B) Malware change the receiver and takes your funds
There are reports of Malware that essentially swap the receiver of when you try to send tokens. You copy the receiver but as you paste it, it gets swapped to a new key, that could be very similar to the one used. This is more prevalent in blockchain systems that rely on public keys instead of account names for transfers.
'https://us.norton.com/internetsecurity-malware-what-is-a-trojan.html'C) Device is lost or breaks
Hardware faults? Spouse spills a glass of water on it? You drop it? Whatever the reason is, don’t risk your shit by only having 1 copy of whatever way you are storing your private keys and passwords.
Now, before your device breaks, go create backups, and then continue this article.
D) You have weak password
E) The service is storing your password poorly
The following video will be a deep dive into why, and how easy it is to crack passwords that are stored poorly in a website or program.
TLDR,
most (all?) places store a hash of your password, and when you enter a password the service checks if the hash becomes the same and if it is, you get to login. The problem is that people use really simple passwords so they are easily guessable. Dictionary words are really bad, even if combined with simple number combinations.
If your password is password123, and stored with md5sum, the hash will look like this: 482c811da5d5b4bc6d497ffa98491e38
If your password is password123, and stored with sha256sum, the hash will look like this: Ef92b778bafe771e89245b89ecbc08a44a4e166c06659911881f383d4473e94f
When choosing your password, do not add words from dictionaries, dates, pets, names, locations or numbers in a sequence, and make sure it’s a longer password. Preferably use a password manager with randomly generated passwords.
F) Your passwords/email combination are leaked
There are tons of hacked databases of user credentials that are leaked and available on the internet. And if not, there are also ways to intercept and get your emails without you noticing and use it to change password and login to the intended services.
Perfect reason to add a secure 2fa on top of as many places as you can.
Below you can see a few reasons why you should take care of your shit and use different password combinations. Please don't use the same email for all the exchanges you use..

G) Trojans can take your clipboard (everything you copy and/or paste)
This is scary as you may not notice it exists, and if you do, it may be too late. https://www.bleepingcomputer.com/news/security/evrial-trojan-switches-bitcoin-addresses-copied-to-windows-clipboard/
The above linked program doesn’t only steal your keys, or swap links, it takes your password and other information. It will also locate your bitcoin wallet in your machine and steal that alongside your password… They sell this software for $27…
This means that if you have this installed on your machine, and you store wallet files, passwords, private keys etc. They already have all this information if you accessed it while the program is present.
Are you starting to understand why you shouldn’t have the owner key on this device?
H) Rootkits installed in your device
“A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed and often masks its existence or the existence of other software.”
These rootkits are often installed by themselves from malware. To prevent these you need to upgrade your computer OS frequently, and even if you do it’s not certain that you will know it exists. And if there’s a rootkit installed on your device, they can do whatever they want.
I) You enter your mnemonic phrase at a phishing attempt
Mnemonic phrases should be treated with respect, and keep very safe. Don’t just store them in a text document or somewhere online. Add them to an encrypted file and store that securely with multiple backups.
Lately there have been phishing and different scam attacks on multiple places like websites and over telegram where they try to get you to post these phrases. One argument they use is that they need to upgrade your public key to the next version… please don’t trust this process. Just a few days ago I heard about a dude that lost $70k from an attempt like this…
J) Signing malicious transactions
This is done on malicious DAPPs and wallets, you may even think that you are doing what you are supposed to, but suddenly your keys are swapped and you no longer have access to your account. This has happened with multiple scams on EOS, and can usually be prevented by properly reading what the tx is trying to do on your device. If the transaction states “updateauth” and you did not want to do that… then it’s probably trying to swap your keys.
Adding custom permissions for your dapps prevent this, cus even if they try to do it, they can’t.
K) Autofill on field to wrong address
Quite a sad situation, the autofill of addresses on EOSIO sites as bloks is there to help the user. But since scammers have bought account names that are very similar to the exchanges account names, you can easily have the wrong account entered and send funds to the wrong place.
This can be prevented by copying the name and memo from the exchange when you are doing such a transfer. Unless you have malware that changes what you copy.. So always double check what you add.
L) Private key is lost and not properly backed up
CREATE MULTIPLE BACKUPS OF YOUR PRIVATEKEYS!!!
Just do it… and store them on a few USB sticks, laminated papers or hardware wallet.. Whatever way you feel is the best for you. As long as you make copies, don’t be lazy and regretful…
M) Password is forgotten
🙁 a risk of using more secure passwords. If you don’t already use a password manager, start now. There are multiple options available. I recommend using one where you control the file, as long as you create MULTIPLE backups of those files.
N) Using Public WI-FI
The owner of the network, or a hacker, is able to log what you send out of your machine and use that against you at a later point. So whenever you feel like connecting to a public WIFI endpoint, expect them to know whatever you are doing, and log all information, it’s safest that way.
