Wireguard is a private VPN network which we use within our operation to connect our internal infrastructure. As well as peering our nodes with trusted entities to guarantee a open peer. It is a well tested and reliable method used on multiple EOSIO chains with great results.
There are multiple reasons for setting up a private peering network, specially between producers. The main reason is to guarantee an open and available peer. An overfilled peer can lead to nodes that are unable to connect with each other. This has been seen at multiple occasion on EOS and other EOSIO chains.
How much traffic do we experience at our public p2p endpoints?
This data comes from our public peering and represent yesterdays traffic. Data is from EOS (our nodes with most traffic)
Incoming 2.9TB
Outgoing 2.3TB
We have a few hundred open slots that are almost always completely filled. Opening up for even more peers has so far led to an increase in traffic and those peers being jammed as well. This is one of the stronger arguments for private peering to make sure all producers are properly peered.
How to get it done
install Wireguard and Resolvconf, the latter is needed for wireguard to run
$ apt-add-repository ppa:wireguard/wireguard
$ apt update && apt install wireguard resolvconf
Generate keys and configuration file
Generate your private key, public key and create your config file. You can name them however you see fit.
$ cd /etc/wireguard
$ umask 077
$ wg genkey > private_key
$ wg pubkey < private_key > public_key
$ cat private_key >> wax.conf
$ cat public_key >> wax.conf
You will also need to open a port in your firewall, on UDP.
Configuring your wireguard
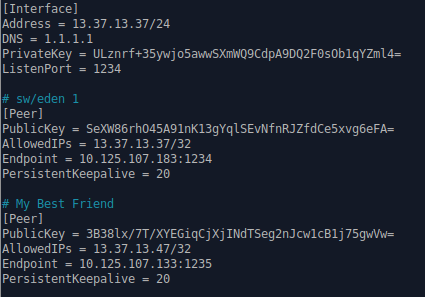
If you followed the above steps, you will now find 2 keys inside your wax.conf.
The first is your private key and the second is your public key.
All you will see are two keys. To set it up you simply need to create the following format. We add our own peer in the list for ease of usage for the future. The names are simply for your own management.
Launching your Wireguard interface
$ wg-quick up wax
To shut it down:
$ wg-quick down wax
Now it's up and running!
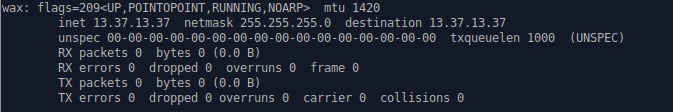
You can see your network over at `ifconfig`
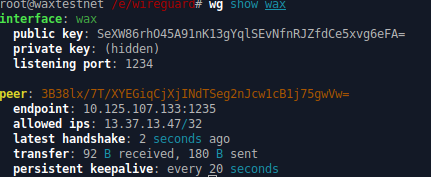
$ wg show wax
wg show will provide you with the status of the endpoints you have added in your Wireguard.
If you have successfully configured your setup (and your friend has done the same) you will get a handshake.
Now either make sure nodeos or a load balancer is listening to the wireguard interface.
Now it is all set for peering over Wireguard. Enjoy!
